Should you Invest in Holiday Ethernet ? ... relying on WiFi whilst on holiday or a business trip is often not the ideal solution, let's take a look at some alternatives.
I am the 'Geek Ambassador' for Hotspot Shield ...
Get behind the Shield here.

Should you Invest in Holiday Ethernet ? ... relying on WiFi whilst on holiday or a business trip is often not the ideal solution, let's take a look at some alternatives.
I am the 'Geek Ambassador' for Hotspot Shield ...
Get behind the Shield here.
The amount of hassle you will face if someone guesses your password and gains access to your mobile phone and/or online accounts is no joke. In this video I discuss various password tips, tricks and advice.
I am the 'Geek Ambassador' for Hotspot Shield ...
Get behind the Shield here http://bit.ly/hshield
Stay safe online, don't get caught out by some of the very clever tricks put in place to get your information.
I am the 'Geek Ambassador' for Hotspot Shield ...
Get behind the Shield here.

Intel has agreed to buy a security software startup for $20 million, boosting its capabilities outside of its core processor business.
The Santa Clara, Calif., chip giant has reached a deal to acquire Sensory Networks, spokesmen from the two companies confirmed to CNET on Tuesday. Both declined to provide deal terms, but Intel said revenue contributions from the acquisition are not material to the company. The Sydney Morning Herald, which earlier reported the news, said Intel will pay about $20 million for the startup...
Read the full story here... Source: CNET
Earlier today I posted a video on the Geekanoids Channel, which essentially was meant to be a bit of fun. However, on looking over the claims Apple made during their Keynote announcement of this technology, their video highlighting it and their website, it has made me question just how secure Touch ID is.
Essentially, this new technology is meant to provide iPhone 5s users a way of securing their device, which can then only be unlocked by their fingerprint(s). Supposedly much more secure than a password.
During the keynote presentation, Phil Schiller said that the sensor scans through the the LIVE layers of your skin. This was also highlighted during their video presentation on the feature, which adds that the sensor essentially takes a "high resolution image of your fingerprint from the sub-epidermal layers of your skin".
From the various claims, I would imagine many people, like myself, were convinced this offers a very high level of security. The words "Live Layers" surely mean that the finger unlocking the iPhone 5s has to be on a living person and not an inanimate object. Surely Apple had thought of this. According to Apple, Touch ID only works by taking a high resolution images of the "sub-epidermal layers of your skin". If this is the case, why does the technology get fooled by a hotdog (aka wiener, sausage, frankfurter)? Surely, the hotdogs that I purchased from the supermarket to make my video were not alive! They certainly were not barking, mooing, or clucking. If such manufactured objects can be used to fool the system, then surely identical objects could be used to unlock multiple devices. I can see it not being long before Touch ID is truly hacked and cracked.
I have brought this to Apples attention, giving them the right to reply, in the hope they will further explain the technology. If we get a reponse, the update will be published here.
OK, OK, so this is not the sort of fishing that will put dinner on the table for you and your family. However, the advice in the video below may help you avoid the criminals phishing for your personal information. Sometimes the trap is so well hidden that even the most experienced can be fooled into clicking a dubious link. Watch the video for more info.
I am the 'Geek Ambassador' for Hotspot Shield ...
Get behind the Shield here http://bit.ly/hshield

The U.S. government has demanded that major Internet companies divulge users' stored passwords, according to two industry sources familiar with these orders, which represent an escalation in surveillance techniques that has not previously been disclosed.
If the government is able to determine a person's password, which is typically stored in encrypted form, the credential could be used to log in to an account to peruse confidential correspondence or even impersonate the user. Obtaining it also would aid in deciphering encrypted devices in situations where passwords are reused.
"I've certainly seen them ask for passwords," said one Internet industry source who spoke on condition of anonymity. "We push back."
A second person who has worked at a large Silicon Valley company confirmed that it received legal requests from the federal government for stored passwords. Companies "really heavily scrutinize" these requests, the person said. "There's a lot of 'over my dead body.'"
Some of the government orders demand not only a user's password but also the encryption algorithm and the so-called salt, according to a person familiar with the requests. A salt is a random string of letters or numbers used to make it more difficult to reverse the encryption process and determine the original password. Other orders demand the secret question codes often associated with user accounts...
Read the full story here. Source: CNET
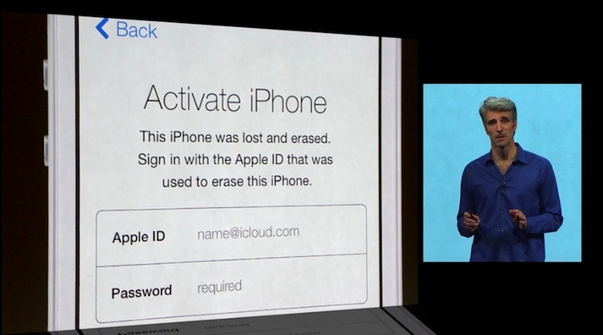
After launching an investigation into the anti-theft practices of smartphone manufacturers like Apple, New York Attorney General Eric Schneiderman and San Francisco District Attorney George Gascón will today test how Apple’s Activation Lock feature holds up against determined thieves, reports CNET.
First introduced at WWDC, Activation Lock is designed to prevent Find My iPhone from being deactivated, which keeps stolen iPhones from being wiped and reactivated. The feature is included in iOS 7, which is expected to be released to consumers this fall.
Gascón and Schneiderman are planning to bring in security experts from the Northern California Regional Intelligence Center to attempt to bypass Activation Lock in order to gain access to an iPhone. The security team will also test the Lojack for Android software on a Samsung Galaxy S4.
"While we are appreciative of the efforts made by Apple and Samsung to improve security of the devices they sell, we are not going to take them at their word," Schneiderman and Gascón said in a joint statement. "Today we will assess the solutions they are proposing and see if they stand up to the tactics commonly employed by thieves."
The two officials have pushed for greater anti-theft measures from cell phone manufacturers after a spike in mobile device thefts. While carriers agreed last year to develop a centralized database to track stolen phones, it has proven to be largely ineffectual. Both Gascón and Schneiderman have stated that they believe Activation Lock is an inadequate theft deterrent and Gascón has urged Apple to implement a "kill switch" that would permanently disable stolen iOS devices.
The results of the Activation Lock investigation are expected to be released later today.
Source: Mac Rumours

While it’s not clear just why the app would do this, or what purpose it has for doing so, the Facebook app for Android is taking your phone number the first time you open it up. Without even logging in, the app takes your number and stores it on the Facebook servers. You don’t need a Facebook account, or even initiate an action within the app. Simply having it and opening it will allow the app to take your phone number.
Norton discovered this security flaw during routine testing they perform on apps for their Mobile Insight security app. According to Norton, their testing methods are sound:
Through automatic and proprietary static and dynamic analysis techniques, Mobile Insight is able to automatically discover malicious applications, privacy risks, and potentially intrusive behavior. Further, Mobile Insight will tell you exactly what risky behavior an application will perform and give you specific, relevant, and actionable information.
-norton
Norton then reached out to Facebook, who claimed to be unaware of the issue. They told Norton they“did not use or process the phone numbers and have deleted them from their servers”, and said they had no knowledge of the issue. Norton also notes that Facebook is not the only app doing this, or even the worst offender. They promise more information on other culprits in coming weeks, but we’re still curious why Facebook would take numbers from a device that wasn’t even logged in. If I were to download the app, then open it to see what it looked like out of curiosity, my number would then be uploaded to the Facebook server.
We’re not ready to call Facebook nefarious on this account. Giving them the benefit of the doubt, even in the face of all their other security flaws, we’ll chalk this up to another error on their part. What this does do is bring into focus app permissions, and how important they are. Perhaps more importantly, how they can be abused by the app publisher, and ignored by users as fine-print.
Source: Android Authority
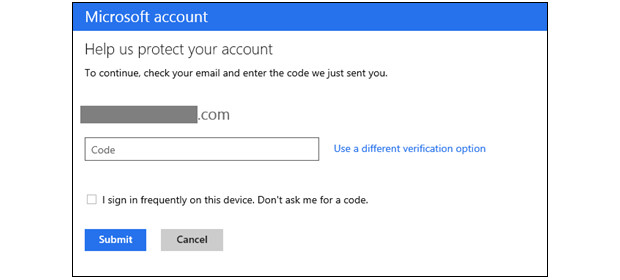 Everyone else is doing it, so why not Microsoft, right? The company has been accused of playing the "me too" game in the past, but we're not going to complain when the the end result is better security. As we learned from a leak last week, Redmond will begin enabling two-step verification for Microsoft accounts. The switch will get flipped for everyone over the next few days and, with email, Xbox Live and Skype (just to name a few) associated with the service formerly known as Live, it's never been more important to keep it locked down. (Especially when others are learning this lesson the hard way.) The two-factor gateway is purely opt-in, except where it's already been required: editing credit card information and accessing SkyDrive from a new computer. There's even a dedicated authenticator app for Windows Phone 8, which works whether or not you've got an internet connection. There's loads more detail at the source and you can check to see if the feature has been turned on for your account at the more coverage link. And if you can, we strongly suggest you turn it on. Like, now.
Everyone else is doing it, so why not Microsoft, right? The company has been accused of playing the "me too" game in the past, but we're not going to complain when the the end result is better security. As we learned from a leak last week, Redmond will begin enabling two-step verification for Microsoft accounts. The switch will get flipped for everyone over the next few days and, with email, Xbox Live and Skype (just to name a few) associated with the service formerly known as Live, it's never been more important to keep it locked down. (Especially when others are learning this lesson the hard way.) The two-factor gateway is purely opt-in, except where it's already been required: editing credit card information and accessing SkyDrive from a new computer. There's even a dedicated authenticator app for Windows Phone 8, which works whether or not you've got an internet connection. There's loads more detail at the source and you can check to see if the feature has been turned on for your account at the more coverage link. And if you can, we strongly suggest you turn it on. Like, now.
[Source: Engadget]
 Soon after word hit about the unbelievably easy Apple ID exploit, Apple has responded by saying it’s already working on a fix. As it should be. If it’s not happening on the mobile side, issues are springing up elsewhere.
Soon after word hit about the unbelievably easy Apple ID exploit, Apple has responded by saying it’s already working on a fix. As it should be. If it’s not happening on the mobile side, issues are springing up elsewhere.
In a statement to The Verge, the company lamented the glaring issue and said it takescustomer privacy very seriously. Let’s hope Apple can tie this one up quick, too. All someone needs to take control of someone else’s Apple ID is their email and date of birth—you can get that kind of information on Facebook very easily.
As of now, Apple has taken down its iForgot password reset tool as a temporary solution. That might be an acceptable short-term fix, but in the long run, let’s hope Apple develops a stricter protocol when reseting a password. Apple IDs are the key to Apple’s content kingdom; if user IDs start running rampant, who knows what kind of backlash the company will face.
[Source: TechnoBuffalo]